Enterprise Policy as Code (EPAC)
EPAC is a tool where you can deploy Azure Policies as code which has many advantages over deploying policies manually via the GUI. The same comparison can be made with Infrastructure as Code (IaC).
It is also recommended by Microsoft employees to use and it has also been published in a Microsoft article back in 2022.
With EPAC, you can deploy:
- Policy Definitions
- Initiatives (Policy Set Definitions)
- Policy Assignments
- Policy Exemptions
- Role Assignments
Implementing EPAC via Azure DevOps
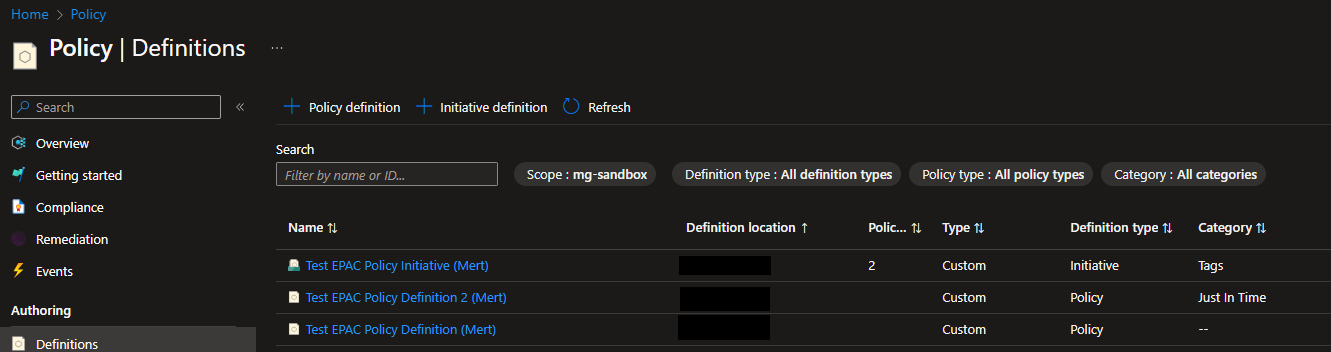
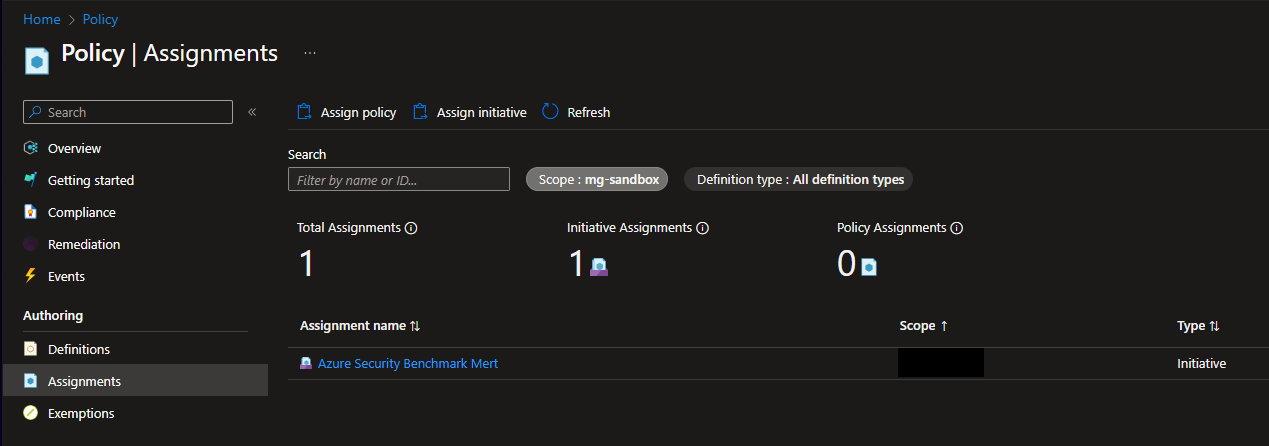
For this example, we will implement
- 2 Policy Definitions
- 1 Policy Initiative
- 1 Policy Assignment
1. Download the repository from the Github-link.
When opening the files you see some folders and files.
Folders
- Definitions: Policy files are stored
- policyAssignments: To store Assignments
- policyDefinitions: To store Policy definitions
- policySetDefinitions: To store Policy initiatives
- Pipelines: File to run the pipeline.
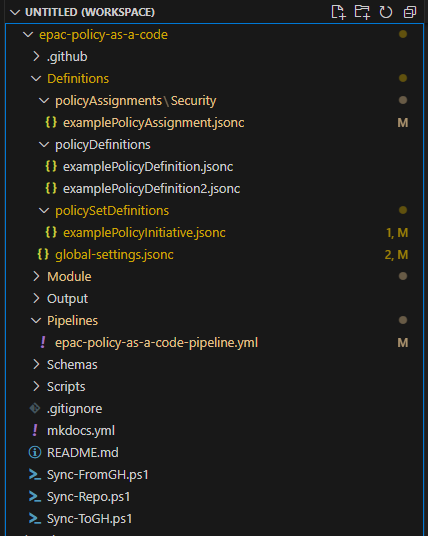
For test purposes, I have created each of above test policies that we can implement.
2. Change the files below:
Files
- epac-policy-as-a-code\Definitions\Security\policyAssignment.jsonc –> change
<mg group ID>to your own Management Group ID - epac-policy-as-a-code\Definitions\policySetDefinitions\examplePolicyInitative.jsonc –> change
<mg group ID>to your own Management Group ID - epac-policy-as-a-code\Definitions\global-settings.jsonc –> change
<mg group ID>to your own Management Group ID and change<tenant ID>to your own Tenant ID
- epac-policy-as-a-code\Pipelines\epac-policy-as-a-code-pipeline.yml –> change
<service connection name>to your own service connection name.
3. Go to Azure DevOps and make sure that:
- An environment-name called ‘test-environment’ has been made under Azure DevOps > Pipelines > Environments
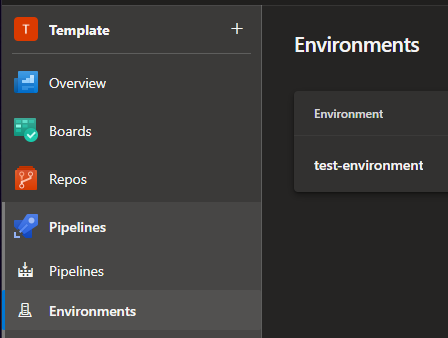
Make sure the Service Principal has Owner rights for the designated management group since it will also assign roles to specific policy and objects.
4. Run the pipeline script and it should show the end results that
- 2 Policy Definitions
- 1 Policy Initiative
- 1 Policy Assignment have been created.
Note: From my own perspective, I’ve polished the pipeline script to run the pipeline simple and easy without having a headache with all sorts of processes they have developed.
Note if using IaC for policies as well
If you’ve deployed policies via IaC and run the EPAC pipeline as well, EPAC will only check its own directory containing the policies and if it does not include the policy files mentioned in the IaC code, then it will remove those policies in Azure as well unless you mention in the EPAC code the exemptions it has to ignore!
More Info
For more information about EPAC, please visit the website https://azure.github.io/enterprise-azure-policy-as-code/

